Access Methods
- 2 Minutes to read
- Print
- DarkLight
- PDF
Access Methods
- 2 Minutes to read
- Print
- DarkLight
- PDF
Article summary
Did you find this summary helpful?
Thank you for your feedback!
Introduction
This document provides an overview of the different access methods available, highlighting their respective pros and cons, compatibility with Rivery, recommendations, and links to more detailed documentation.
Selecting the Optimal Connection Method
| Connection Option | Pros | Cons | Rivery Compatibility | Rivery Recommendation | Documentation |
|---|---|---|---|---|---|
| IP Whitelist | - Simple configuration and management. - No additional resources required. | - Least secure. - Exposes database to the internet. - Higher cost. - Poor performance. - Requires internet ingress connection. | ✅ | LESS RECOMMENDED Use for open/demo databases with public data only. | Rivery's Whitelist IPs - Access Methods |
| SSH Tunnel | - Minimal resource requirements. - Easy setup. - Database not exposed to the public internet. - Quick ingress traffic. | - Poor scalability with many connections. - Requires instance configuration. - SSH instance must be internet-accessible with IP whitelisting. | ✅ | MEDIUM RECOMMENDED Use if no other internal AWS options are available. | SSH Tunnel - Access Methods |
| AWS PrivateLink | - Minimal resource needs. - Low to medium infrastructure effort. - Unlimited scalability. - Secure and managed by AWS. - Easy maintenance. | - May require additional Lambda provisioning for some resources. - Only works within the same AWS region. | ✅ | HIGHLY RECOMMENDED Ideal for internal AWS resources. | AWS PrivateLink - Access Methods AWS PrivateLink Setup for Snowflake Connection in Rivery |
| Amazon Redshift PrivateLink | - Direct integration with Amazon Redshift. - High security by avoiding public internet. - Reduced latency for data access. | - Limited to AWS regions. - Requires specific configuration for Amazon Redshift. | ✅ | HIGHLY RECOMMENDED Best for secure connections to Amazon Redshift. | Amazon Redshift PrivateLink |
| Azure Private Link | - Direct and secure connection to Azure resources. - Managed by Azure for scalability and low latency. - Simplified network configuration. | - Requires additional Azure configuration. - Limited to Azure-specific environments. | ✅ | HIGHLY RECOMMENDED Best for secure connections within Azure. | Azure Private Link Setup |
| Google Private Service Connect Setup | - Secure and private connectivity to Google Cloud resources. - Managed by Google for scalability and low latency. - Simplified network setup. | - Requires Google Cloud environment. - Limited compatibility outside Google Cloud. | ✅ | HIGHLY RECOMMENDED Best for secure connections within Google Cloud. | Google Private Service Connect Setup |
| VPC Peering | - Minimal resource requirements. - Low to medium infrastructure effort. - Unlimited scalability. - Operates on AWS network backbone. | - Exposes internal IPs to Rivery and vice versa. - Potential IP collision. - Requires strict security measures. - Inflexible with VPC changes. | ❌ | NOT AVAILABLE Not supported due to high-security compliance. | |
| VPN Site-To-Site Customer Gateway | - Unlimited scalability. - Operates on AWS network backbone. | - Medium to high effort. - Requires in-depth configuration and maintenance. - Less flexible with VPC changes. | ✅ | MEDIUM RECOMMENDED Best for connecting on-premise resources in internal VPC. | Integrating Rivery with VPN |
| Reverse SSH | - Low resource requirements. - Client-initiated ingress connection. | - Requires knowledge of proxy servers. - Fully managed by the client. - Less flexible with VPC changes. - Limited scalability compared to VPN. | ✅ | MEDIUM RECOMMENDED | Reverse SSH Tunnel |
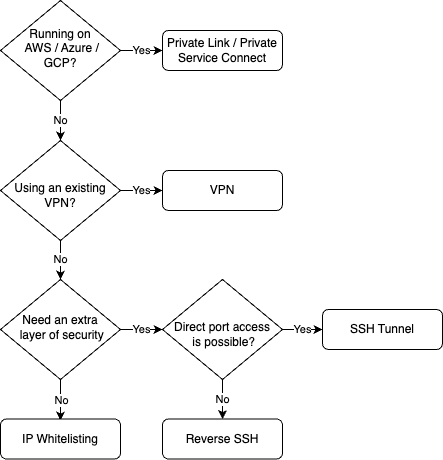
To help you choose the most suitable connection method, refer to the flowchart below:
Was this article helpful?

