- 2 Minutes to read
- Print
- DarkLight
- PDF
Google Private Service Connect Setup
- 2 Minutes to read
- Print
- DarkLight
- PDF
Google Private Service Connect is exclusively available to users on the Enterprise plan
Introduction
This guide outlines how to use Private Service Connect (PSC) to establish a connection to a Cloud SQL instance using Google Cloud's command-line interface (CLI).
With Private Service Connect, you can connect to either a primary Cloud SQL instance or its read replicas from various Virtual Private Cloud (VPC) networks, regardless of whether they belong to different groups, teams, projects, or organizations.
Prerequisite
Ensure that the gcloud CLI is installed and configured with the appropriate permissions before proceeding.
Step 1: Create the Database Instance with PSC
Use the following command to connect to an instance via Private Service Connect using the Google Cloud CLI.
gcloud sql instances create INSTANCE_NAME \
--project=PROJECT_ID \
--region=REGION_NAME \
--enable-private-service-connect \
--allowed-psc-projects=rivery-cloud-2017 \
--availability-type=REGIONAL \
--no-assign-ip \
--tier=MACHINE_TYPE \
--database-version=DATABASE_VERSION \
--enable-bin-log
Make the following replacements:
- --project: Specifies the Google Cloud project ID.
- --region: Defines the region for the SQL instance (for example, us-east1).
- --enable-private-service-connect: Enables Private Service Connect for the instance.
- --allowed-psc-projects: Allows specific projects (in this case, rivery-cloud-2017) to connect via PSC.
- --availability-type: Sets the availability type, ensuring redundancy with REGIONAL.
- --no-assign-ip: Ensures the instance is created without an external IP.
- --tier: Sets the instance tier, db-g1-small (a lightweight configuration).
- --database-version: Defines the database version to be used.
- --enable-bin-log: Enables binary logging for replication and point-in-time recovery.
Step 2: Verify the Instance Creation
After creating the instance, confirm its successful creation by describing it:
gcloud sql instances describe INSTANCE_NAME \
--project=PROJECT_ID
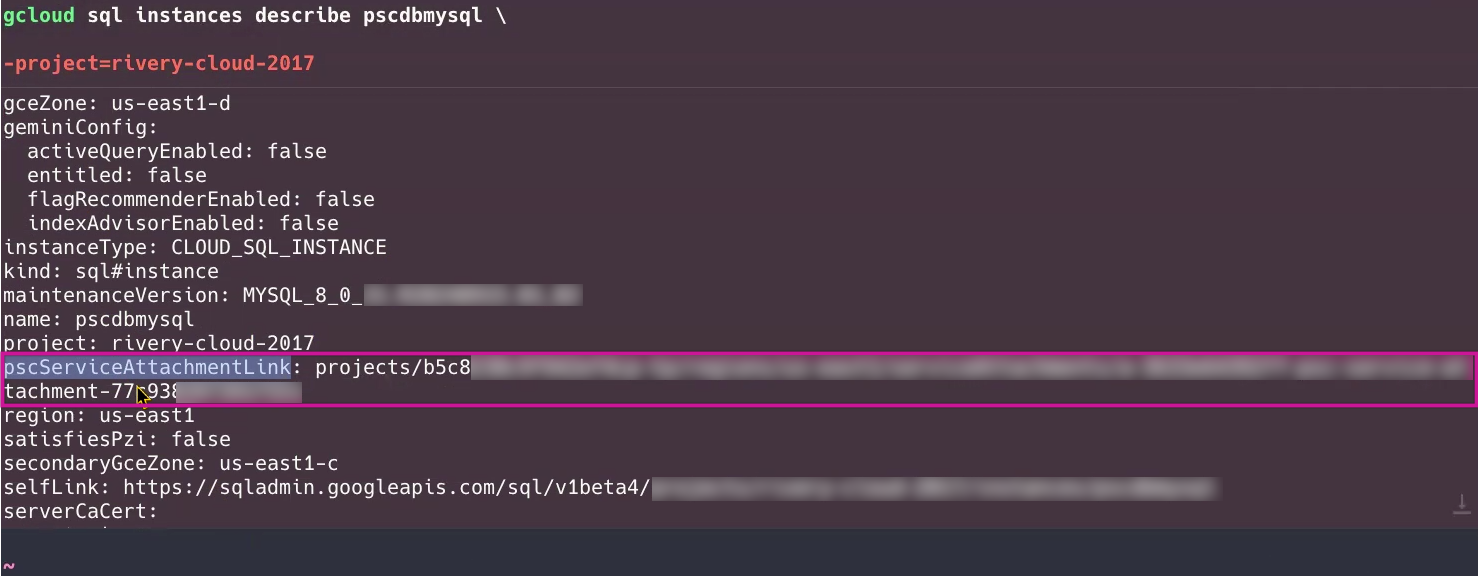
This command retrieves the details of the pscdbmysql instance. Look for the pscServiceAttachmentLink in the output, which shows the service attachment link for the PSC.
Example output
pscServiceAttachmentLink: projects/b5c8238c9f342cf4cp-tp/regions/us-east1/serviceAttachments/a-3673e65382ff-psc-service-attachment-77c938123391f551
Step 3: Create a Forwarding Rule for the PSC
To route traffic via Private Service Connect, a forwarding rule needs to be created. First, create an address for the forwarding rule.
gcloud compute addresses create ADDRESS_NAME \
--project=PROJECT_ID \
--region=REGION_NAME \
--subnet=SUBNET_NAME \
--addresses=INTERNAL_IP_ADDRESS
Next, create the forwarding rule using the PSC service attachment link retrieved in Step 2.
gcloud compute forwarding-rules create ENDPOINT_NAME \
--address=ADDRESS_NAME \
--project=PROJECT_ID \
--region=REGION_NAME \
--network=NETWORK_NAME \
--target-service-attachment=SERVICE_ATTACHMENT_URI \
--allow-psc-global-access
Make the following replacements:
- --address: Specifies the internal IP address created in the previous step.
- --target-service-attachment: Links the forwarding rule to the PSC service attachment.
- --allow-psc-global-access: Enables global access to the PSC.
Step 4: Firewall Configuration
If you encounter issues connecting, ensure the firewall settings allow traffic between the relevant VPCs (Virtual Private Clouds).
- Navigate to VPC Network > Firewall in the Google Cloud Console.
- Create firewall rules to allow traffic between the necessary subnets or networks.
Make sure to set up these rules in both accounts if you are working with different projects or VPCs.
Step 5: Configuring the Private Service Connect
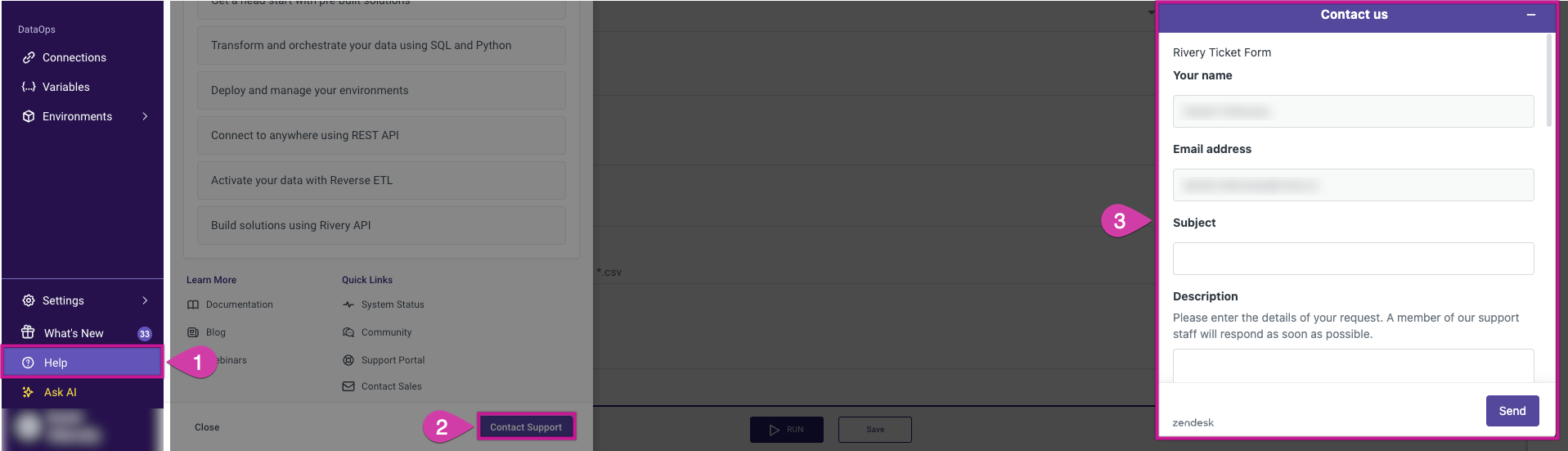
To proceed with the configuration of the Private Service Connect, follow these steps:
Forward the Output: After generating the
pscServiceAttachmentLink(step 2), please send this information to our Support team for further configuration.Open a Support Ticket:
- Navigate to the Help menu in the console.
- Open a new Support ticket and include the full output of the
pscServiceAttachmentLink.
Providing this information will allow our Support team to complete the Private Service Connect setup.
- Follow-up with Support: After the ticket submission, the Support team will contact you and provide an IP address. You will need to add this IP address to your source configuration.

